Network Data Security System Design with High Security Insurance
Design Introduction
Because of the availability of relatively large bandwidth, computers worldwide are connected via a
network. Computer users can transfer information and exchange data easily on the Internet, and as a
result, many network data servers have been set up. With this growth, ensuring data security during
storage and transmission has become very important. In our project, a channel coding and encryption
system protects data, ensuring data security in case of network invalidation. It also prevents data loss
for cases in which a single packet of data is revealed (including losing an encryption key). Our goal is
to make a new network data security system with high-security insurance.
A traditional network data security system (e.g., network-attached storage devices or a storage area
network) achieves high security through encryption/decryption algorithms such as advanced encryption
standard (AES), data encryption standard (DES), RC6, and other symmetric key cryptosystems.
However, with these schemes data errors have become more frequent, particularly as network
transmissions enter the gigabit per second (Gbps) range. Therefore, our new network data security
system must consider data accuracy and privacy.
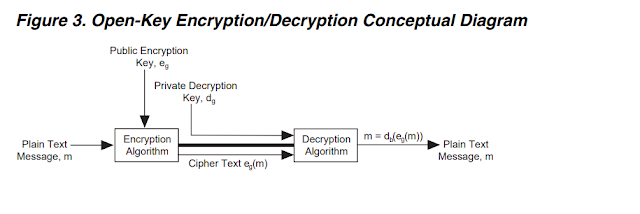
We used the AES block cipher to encrypt the data and we used an RSA algorithm to encrypt the AES
key. The key and encypted data are encoded using a Reed-Solomon (RS) encoder and stored, via
Ethernet, onto multiple archive data servers. When the data is read from the server, the reverse process occurs and decoding is performed on each server.
Because of fault tolerance mechanisms, the server works normally even when data errors occur during transmission or if the server is damaged. To develop our proposed embedded system, we used a Nios® II processor (a 32-bit RISC soft-core processor) to integrate various peripherals that we downloaded via the Internet. The design’s AES, RS encoder, RSA algorithm, and network communication protocol require many look-up tables (LUTs) and hardware design. We used system-on-a-programmable-chips (SOPC) concepts and hardware/ software co-design to shorten the design process.
The Nios II processor supports user-defined custom instructions as well as hardware acceleration. It can also perform other functions such as processing, controlling, decision making, and ordering. These features allow the software designer to write the control flow program in C/C++, while most of the computing is done in hardware. The software application includes a custom instruction that operates as a high-speed, hardware-accelerated computing module. In addition to supporting custom instructions, the Nios II Integrated Development Environment (IDE), which includes the GNU C/C++ assembler and Eclipse IDE, is ideal for the entire design process. Furthermore, the designer can perform simulation, development, debugging, integration, and validation in real time on the Development and Education (DE2) board. All of these features make development efficient. Design Concepts Using hardware/software co-design helped us complete the network data security system rapidly. The design can be divided into 3 parts, as shown below:
■ System—The Nios II processor performs the major system control functions. These functions include flow control, general computing, system monitoring, event decision making, receiving and sending data, user interfacing, and implementing an interrupt service routine.
■ Hardware—The hardware includes an RS encoder, AES, and RSA high-speed operation components, charge-coupled device (CCD) image capture components, dual-port SDRAM controller, Ethernet controller, VGA controller, and SRAM controller.
■ Software—The software provides a testing and validating platform for the communication between the software and the hardware. We also use it for software simulation and development.
Figure 1 shows the test platform for the system.
The core infrastructure has the following elements, as shown in Figure 6:
■ High-Speed Data Processor—Includes the RS encoder/decoder, AES, and RSA operations.
■ CCD Controller—Connects to the CCD camera via a programmable I/O (PIO) and direct memory access (DMA) to capture images.
■ VGA Controller—Displays the image captured by the CCD camera on a computer display.
■ SDRAM Controller—Reads/writes data at high speed.
■ Network Controller—Performs network card initialization, receives packets, and sends interrupt processing and user datagram protocol (UDP) communications.
■ System Software—Provides LUT operation, hardware core component control, peripheral control, operation control, data flow control, interface control, interrupt control, etc.
Application Scope Our project can be used in the following applications:
■ Distributed archive security system
■ Archive server
■ Network hard drive or mail server
■ High-speed database storage system
■ Disk array Target Users Our project targets the following users:
■ Companies that need a high-security data storage system
■ Designers of network data security systems that require high security insurance
■ Portable communication or storage system producers
■ Personal data storage system designers Development Board Our design uses the Altera® DE2 development board, which contains a Cyclone® II EP2C35F672C6 FPGA, EPCS16 serial configuration device, 8-Mbyte SDRAM, 512-Kbyte SRAM, 4-Mbyte flash, secure digital (SD) memory card slot, 10/100 Ethernet, RS-232 port, infrared port, etc. See Figure 8.
Figure 8. DE2 Development Board
Function Description
This section describes the function of our design.
Development Steps We used the following general steps to implement the design.
1. Implement the design’s operational blocks (AES, RSA, and RS encoding) in HDL (VHDL and Verilog HDL) using the Quartus® II development environment.
2. Capture an image using a CCD camera, which is displayed in real time with a VGA controller. The captured image is the data source to be encoded and encrypted. The SDRAM image data on the DE2 development board outputs from the computer over the network.
3. Transmit data for real-time encoding/decoding using Ethernet and DMA control.
4. Develop custom instructions to implement the RSA decoder. Return the result directly to the ALU.
5. Build the entire system using SOPC Builder. Complete the hardware/software co-design and demonstration.
6. Simulate AES-128 encryption and RS (6,4,1) encoding/decoding with C++ Builder.
7. Use C++ Builder to complete the network communication GUI interface with the DE2 development board.
8. Simulate several data servers with one PC (for example, it could simulate a situation in which the service of one or more servers is suspended).
9. Test the systems using test data. Implementation This section describes how we implemented the design. Create the Components Using the Quartus II software version 5.1, we created the AES, RSA and RS encoding functions in VHDL and Verilog HDL.
Specifically, we:
1. Analyzed the AES algorithm and developed its four key components. We integrated the encoding and decoding functions for increased CPU efficiency and data property. This functionality is recursive.
2. Analyzed the RS function. We implemented the RS decoder and encoder using a general reliable error-correcting mechanism.
3. Created all components according to the input requirements: multiplier, square, and finite field inverse, KeyExpansion, (Inv)SubBytes, (Inv)ShiftRows, (Inv)MixColumes, (Inv)AddRoundKey, RSA decoder, RS decoder, and RS encoder.
4. Developed the VHDL components using the Quartus II software version 5.1, and performed functional validation and timing simulation.
Capture and Display the Image We captured an image via a CCD camera and displayed it in real time on-screen using a VGA controller. The captured image is the data source to be encoded and encrypted. The following steps describe this process.
1. Use Verilog HDL to connect the CCD controller and VGA controller with the Nios II processor (using a PIO function) as shown in Figure 9.
2. Display the captured image on-screen using a VGA controller. Alternatively, use the Nios II processor to transmit it back to the PC via Ethernet for use by the software and hardware encryption/decryption and encoding validation.
Figure 9. CCD and VGA Controller
Transmit the Data We implement real-time data encoding/decoding transmission via Ethernet, the USB interface, and DMA control as described in the following steps.
1. Incorporate the Ethernet and USB interfaces by selecting the components in SOPC Builder as shown in Figure 10.
2. Set the arbitration parameter and connect the interfaces with the Avalon bus as shown in Figure 11.
3. Use the Ethernet port to transfer encoding/decoding data between the PC validation platform and the virtual server on the network.
Figure 10. SOPC Builder Components
Figure 11. Avalon Bus and Arbitration
Generate the System
We generated the entire system with SOPC Builder as described in the following steps.
1. Open the Altera-provided Cyclone II standard CPU example.
2. Add the user-defined PIO pins, as shown in Figure 12. Table 2 shows the setting of each pin.
3. Design the system infrastructure with SOPC Builder, and generate the system.h header file, peripheral drives, and EDIF file.
4. Generate the executable file using the GNUPro encoder, which is downloaded to the Cyclone II device after validation and debugging.
Figure 12. Add User-Defined Pins
Table 2. User-Defined Pin Functions
Encrypt and Encode Data
We used C++ Builder to complete 128-bit AES encryption and RS encoding/decoding as described in the following steps.
1. Write a user interface program with C++ Builder. Figure 13 shows an example of the parameter settings.
Figure 13. Parameter Settings
2. Write reference rules according to the specification of the Federal Information Processing Standard Publication 197 and RS encoding concepts.
3. Finish the software testing platform gradually and use the platform as the reference for the whole system (see Figures 14 through 20).
Figure 14. Validate Whether the Encoding/Decoding Is Correct
Graduation thesis...
to be continued...
Because of the availability of relatively large bandwidth, computers worldwide are connected via a
network. Computer users can transfer information and exchange data easily on the Internet, and as a
result, many network data servers have been set up. With this growth, ensuring data security during
storage and transmission has become very important. In our project, a channel coding and encryption
system protects data, ensuring data security in case of network invalidation. It also prevents data loss
for cases in which a single packet of data is revealed (including losing an encryption key). Our goal is
to make a new network data security system with high-security insurance.
A traditional network data security system (e.g., network-attached storage devices or a storage area
network) achieves high security through encryption/decryption algorithms such as advanced encryption
standard (AES), data encryption standard (DES), RC6, and other symmetric key cryptosystems.
However, with these schemes data errors have become more frequent, particularly as network
transmissions enter the gigabit per second (Gbps) range. Therefore, our new network data security
system must consider data accuracy and privacy.
We used the AES block cipher to encrypt the data and we used an RSA algorithm to encrypt the AES
key. The key and encypted data are encoded using a Reed-Solomon (RS) encoder and stored, via
Ethernet, onto multiple archive data servers. When the data is read from the server, the reverse process occurs and decoding is performed on each server.
Because of fault tolerance mechanisms, the server works normally even when data errors occur during transmission or if the server is damaged. To develop our proposed embedded system, we used a Nios® II processor (a 32-bit RISC soft-core processor) to integrate various peripherals that we downloaded via the Internet. The design’s AES, RS encoder, RSA algorithm, and network communication protocol require many look-up tables (LUTs) and hardware design. We used system-on-a-programmable-chips (SOPC) concepts and hardware/ software co-design to shorten the design process.
The Nios II processor supports user-defined custom instructions as well as hardware acceleration. It can also perform other functions such as processing, controlling, decision making, and ordering. These features allow the software designer to write the control flow program in C/C++, while most of the computing is done in hardware. The software application includes a custom instruction that operates as a high-speed, hardware-accelerated computing module. In addition to supporting custom instructions, the Nios II Integrated Development Environment (IDE), which includes the GNU C/C++ assembler and Eclipse IDE, is ideal for the entire design process. Furthermore, the designer can perform simulation, development, debugging, integration, and validation in real time on the Development and Education (DE2) board. All of these features make development efficient. Design Concepts Using hardware/software co-design helped us complete the network data security system rapidly. The design can be divided into 3 parts, as shown below:
■ System—The Nios II processor performs the major system control functions. These functions include flow control, general computing, system monitoring, event decision making, receiving and sending data, user interfacing, and implementing an interrupt service routine.
■ Hardware—The hardware includes an RS encoder, AES, and RSA high-speed operation components, charge-coupled device (CCD) image capture components, dual-port SDRAM controller, Ethernet controller, VGA controller, and SRAM controller.
■ Software—The software provides a testing and validating platform for the communication between the software and the hardware. We also use it for software simulation and development.
Figure 1 shows the test platform for the system.
The core infrastructure has the following elements, as shown in Figure 6:
■ High-Speed Data Processor—Includes the RS encoder/decoder, AES, and RSA operations.
■ CCD Controller—Connects to the CCD camera via a programmable I/O (PIO) and direct memory access (DMA) to capture images.
■ VGA Controller—Displays the image captured by the CCD camera on a computer display.
■ SDRAM Controller—Reads/writes data at high speed.
■ Network Controller—Performs network card initialization, receives packets, and sends interrupt processing and user datagram protocol (UDP) communications.
■ System Software—Provides LUT operation, hardware core component control, peripheral control, operation control, data flow control, interface control, interrupt control, etc.
Application Scope Our project can be used in the following applications:
■ Distributed archive security system
■ Archive server
■ Network hard drive or mail server
■ High-speed database storage system
■ Disk array Target Users Our project targets the following users:
■ Companies that need a high-security data storage system
■ Designers of network data security systems that require high security insurance
■ Portable communication or storage system producers
■ Personal data storage system designers Development Board Our design uses the Altera® DE2 development board, which contains a Cyclone® II EP2C35F672C6 FPGA, EPCS16 serial configuration device, 8-Mbyte SDRAM, 512-Kbyte SRAM, 4-Mbyte flash, secure digital (SD) memory card slot, 10/100 Ethernet, RS-232 port, infrared port, etc. See Figure 8.
Figure 8. DE2 Development Board
Function Description
This section describes the function of our design.
Development Steps We used the following general steps to implement the design.
1. Implement the design’s operational blocks (AES, RSA, and RS encoding) in HDL (VHDL and Verilog HDL) using the Quartus® II development environment.
2. Capture an image using a CCD camera, which is displayed in real time with a VGA controller. The captured image is the data source to be encoded and encrypted. The SDRAM image data on the DE2 development board outputs from the computer over the network.
3. Transmit data for real-time encoding/decoding using Ethernet and DMA control.
4. Develop custom instructions to implement the RSA decoder. Return the result directly to the ALU.
5. Build the entire system using SOPC Builder. Complete the hardware/software co-design and demonstration.
6. Simulate AES-128 encryption and RS (6,4,1) encoding/decoding with C++ Builder.
7. Use C++ Builder to complete the network communication GUI interface with the DE2 development board.
8. Simulate several data servers with one PC (for example, it could simulate a situation in which the service of one or more servers is suspended).
9. Test the systems using test data. Implementation This section describes how we implemented the design. Create the Components Using the Quartus II software version 5.1, we created the AES, RSA and RS encoding functions in VHDL and Verilog HDL.
Specifically, we:
1. Analyzed the AES algorithm and developed its four key components. We integrated the encoding and decoding functions for increased CPU efficiency and data property. This functionality is recursive.
2. Analyzed the RS function. We implemented the RS decoder and encoder using a general reliable error-correcting mechanism.
3. Created all components according to the input requirements: multiplier, square, and finite field inverse, KeyExpansion, (Inv)SubBytes, (Inv)ShiftRows, (Inv)MixColumes, (Inv)AddRoundKey, RSA decoder, RS decoder, and RS encoder.
4. Developed the VHDL components using the Quartus II software version 5.1, and performed functional validation and timing simulation.
Capture and Display the Image We captured an image via a CCD camera and displayed it in real time on-screen using a VGA controller. The captured image is the data source to be encoded and encrypted. The following steps describe this process.
1. Use Verilog HDL to connect the CCD controller and VGA controller with the Nios II processor (using a PIO function) as shown in Figure 9.
2. Display the captured image on-screen using a VGA controller. Alternatively, use the Nios II processor to transmit it back to the PC via Ethernet for use by the software and hardware encryption/decryption and encoding validation.
Figure 9. CCD and VGA Controller
Transmit the Data We implement real-time data encoding/decoding transmission via Ethernet, the USB interface, and DMA control as described in the following steps.
1. Incorporate the Ethernet and USB interfaces by selecting the components in SOPC Builder as shown in Figure 10.
2. Set the arbitration parameter and connect the interfaces with the Avalon bus as shown in Figure 11.
3. Use the Ethernet port to transfer encoding/decoding data between the PC validation platform and the virtual server on the network.
Figure 10. SOPC Builder Components
Figure 11. Avalon Bus and Arbitration
Generate the System
We generated the entire system with SOPC Builder as described in the following steps.
1. Open the Altera-provided Cyclone II standard CPU example.
2. Add the user-defined PIO pins, as shown in Figure 12. Table 2 shows the setting of each pin.
3. Design the system infrastructure with SOPC Builder, and generate the system.h header file, peripheral drives, and EDIF file.
4. Generate the executable file using the GNUPro encoder, which is downloaded to the Cyclone II device after validation and debugging.
Figure 12. Add User-Defined Pins
Table 2. User-Defined Pin Functions
Encrypt and Encode Data
We used C++ Builder to complete 128-bit AES encryption and RS encoding/decoding as described in the following steps.
1. Write a user interface program with C++ Builder. Figure 13 shows an example of the parameter settings.
Figure 13. Parameter Settings
2. Write reference rules according to the specification of the Federal Information Processing Standard Publication 197 and RS encoding concepts.
3. Finish the software testing platform gradually and use the platform as the reference for the whole system (see Figures 14 through 20).
Figure 14. Validate Whether the Encoding/Decoding Is Correct
Graduation thesis...
to be continued...
























Yorumlar
Yorum Gönder